This week, we will be looking at the 3rd Insecure Storage issue and understand its impact on App.
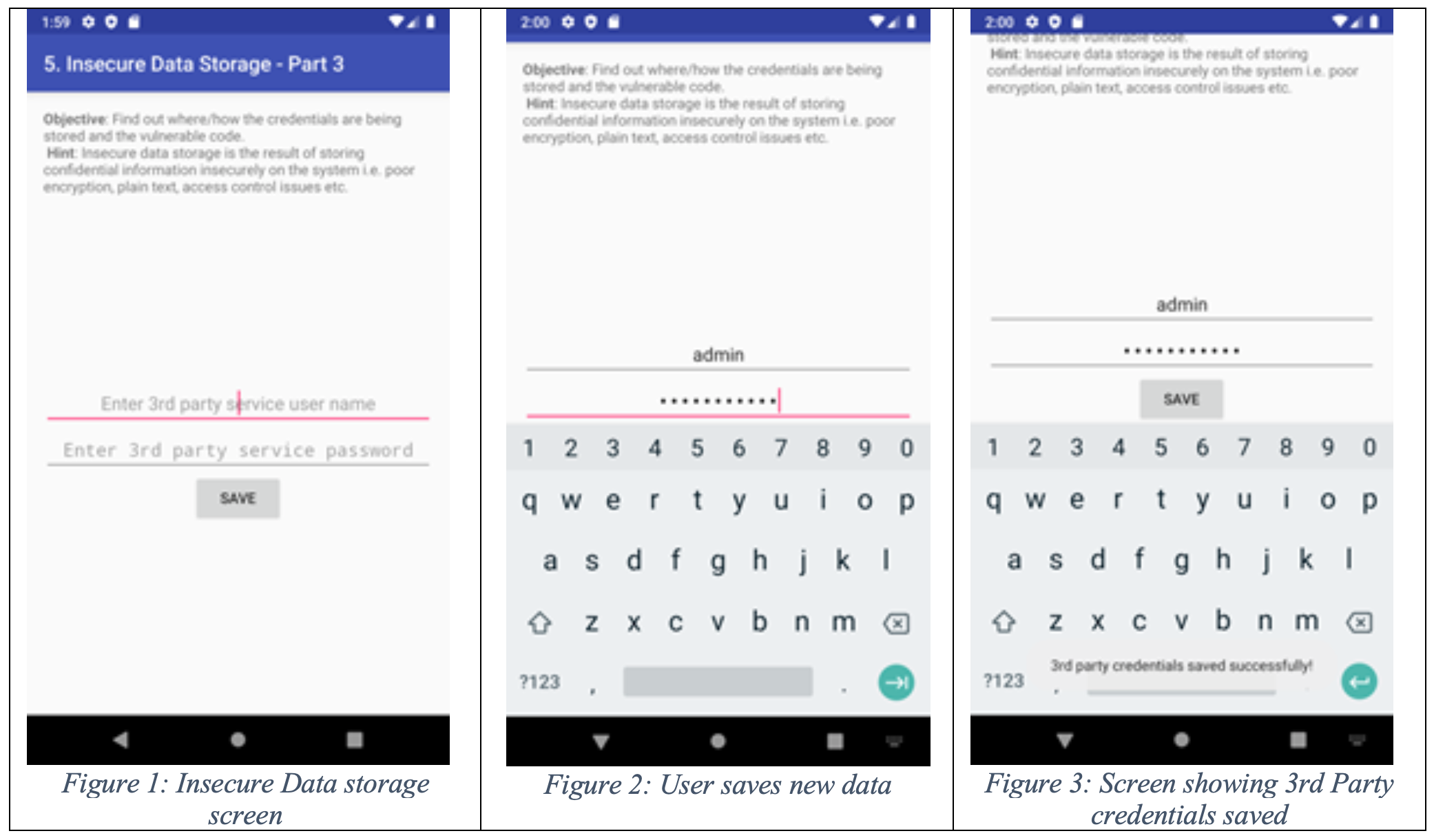
We can see the 3rd part of Insecure Data Storage screen looks same as the previous exercise. New 3rd party service name and password has been entered and saved (username: admin and password123).
Let us walk through the code to understand how the data is stored comparing against the previous exercise.
Open the classes.dex using jadx gui, click on InsecurityDataStorage3Activity under jakhar.aseem.diva.InsecureDataStorage3Activity class. Here the class InsecurityDataStorage2Activity inherits the properties & methods of AppCompatActivity which is another Android class library. There are two methods:
-
- Create
- saveCredentials
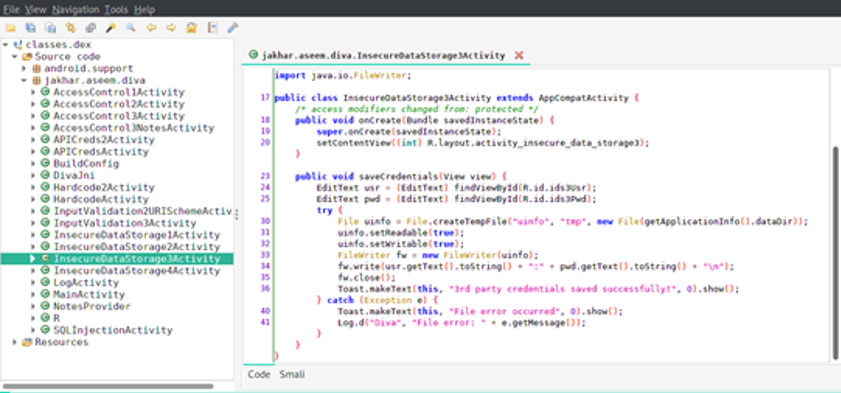
Create method handles creating content view for user to enter data.
Second method saveCredentials saves the user input user/password and saves it to temporary file displaying 3rd party credentials saved successfully. Similar to the previous exercise, error handling takes care of file error related issues and displays a message (if any).
The temporary file is located in “/data/data/jakhar.aseem.diva”. These temporary locations are different for each Android version. So, it’s up to us to find the location.
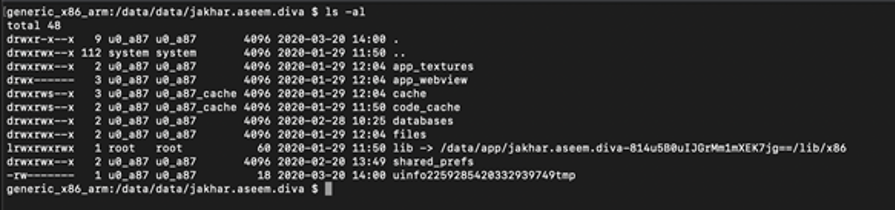
Figure 5: Directory listing on Temporary file location
We can see from the source code from saveCredentials method, there is a function “createTempFile”, which takes first two parameters value as “uinfo” and “tmp”. We can safety assume the temporary file starts with word “uinfo” and “tmp” is also used in the file name. Similarly in adb shell directory listing, there is a file listed uinfo2259285420332939749tmp”. This could be our temporary file, let us read the contents:
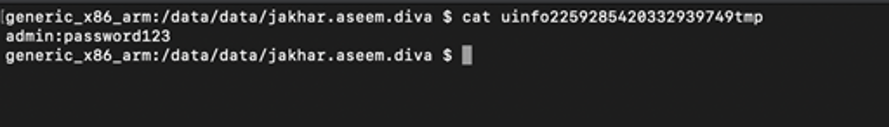
Figure 6: Temporary file contents (Credentials)
We can see the credentials are stored in plain text into temporary file. This is another InsecureStorage vulnerability.
Remediation
Use any encryption technique with Keystore to ensure it is stored securely. Most insecure storage issues can be mitigated in this way.







