In this post we’ll be discussing the topic of Docker and how this could be used to target developers. Most readers will know what docker is, but for those who don’t know, Docker is simply a platform in which to allow applications to be packaged up into a container. These containers are isolated from one another and contain the application and all the necessary components needed to run the application.
Images can be created from these containers which allows for the transferring to other hosts without the application being affected. There is a repository of Docker images Docker Hub which is where the images are downloaded when using “docker pull” command for instance. Individuals across the globe download images every day, however, what would happen if a container image was only setup to comprise one or many organisations?
When viewing Docker Hub there are two main options that can be selected: Official Image and Verified Publisher. These will indicate there will be some authenticity behind the images. For example, here are two images that have these options:
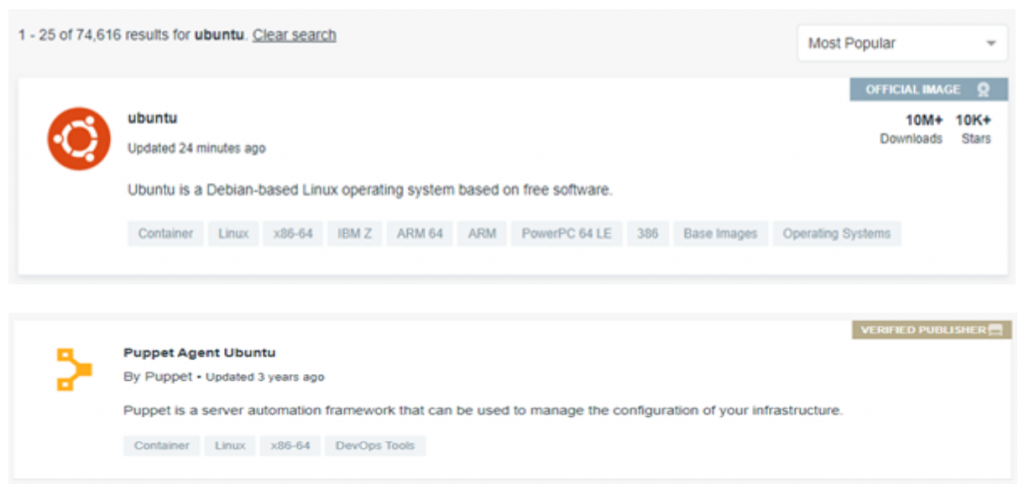
However, not all images have these tags. So, if a malicious image was downloaded and used by a developer to maybe get a sprint completed in time because creating their own would take longer, the potential risk this could introduce may be high.
An example of this would be if an image was used and then introduced into an organisation’s infrastructure but was in fact backdoored allowing a malicious user to access the container. This may seem to be a theoretical idea; however, this was discovered in 2018 here, and some of these were downloaded more than one million times.
Being able to download pre-made containers might seem to be a great idea, but this is can introduce a huge risk. Containers which are used that do not have the tags “Official Image” or “Verified Publisher” should have verification carried out before they are used. Otherwise, provide enough time and resources for containers to be built in-house.







